MainInsights & AnalyticsVulnerabilities on the corporate network perimeter
Vulnerabilities on the corporate network perimeter
349

In this report, we will share the results of automated security assessment of the network perimeter of selected corporate information systems. Scanning was per-formed using the MaxPatrol 8 vulnerability and compliance management system in Pentest mode. More details on MaxPatrol 8 scan modes can be found at the end of this document.
- Positive Technologies experts detected high-risk vulnerabilities on external network resources of 84% of tested companies. Even a low-skilled attacker could exploit 10% f vulnerabilities by using a ready public exploit.
- Half of vulnerabilities can be eliminated by installing software updates.. Systems at 26% of companies are still vulnerable to WannaCry encryption malware.
- At 74% of companies, SSH is available for direct connection from the Internet. One fifth of software vulnerabilities involved OpenSSH errors, which may allow attackers to obtain control over network perimeter resources or breach the company's local network.
- All the companies' perimeters have hosts vulnerable to the SWEET32 attack, and 84 percent of companies are still vulnerable to the POODLE attack. If attackers succeed in exploiting these vulnerabilities, they can extract confidential data from encrypted connections.
Added:08.12.2020
Latest update:11.16.2020
Similar analytics:
 Dr. Web
Dr. WebDoctor Web’s November 2021 virus activity in Russia review
Statistics on virus activity .Read more GK Solar
GK SolarResults of the analysis of the security of Russian companies
New report by Rostelecom-Solar on common vulnerabilities and deficiencies in infrastructure components, employ...Read more Kaspersky Lab
Kaspersky LabFinancial Cyberthreats in 2020
Users in Russia, Germany and Kazakhstan were the most frequent targets of financial malware in 2020.Read more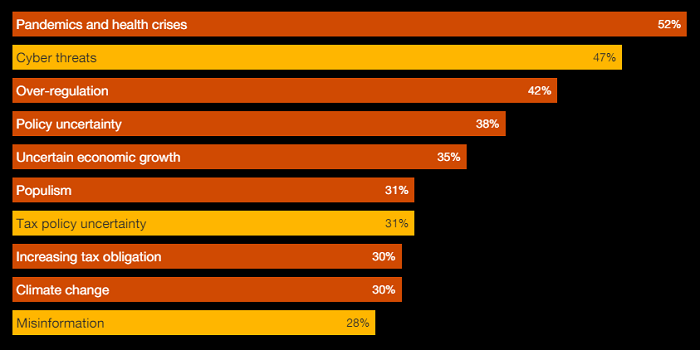 PwC
PwC24th Annual Global CEO Survey
Half of CEOs plan to increase investment in digitalization by more than 10%.Read more
Similar news:
Subscribe to get updates
By clicking the button you agree to Privacy Policy
Add your research
Supported by the Moscow Government
Content and Editorial:tech@ict.moscow
